Safeguarding against cyber threats has become a paramount concern for businesses across all industries. CrowdStrike, a well-renowned cybersecurity company recognized by esteemed industry authorities like Gartner and Forrester, stands at the forefront of safeguarding businesses. With a data-driven approach, CrowdStrike's Falcon platform boasts an astonishing 99% threat detection rate, making it the ultimate choice for industries spanning technology, cloud, service providers, and beyond.
In this blog we delve into CrowdStrike's expertise in endpoint protection, strategies to combat ransomware, the importance of protecting an organization's Active Directory (AD) while simultaneously addressing challenges that occur, and how to leverage the Falcon platform to keep their security posture intact.
Ransomware: A Two-Part Problem
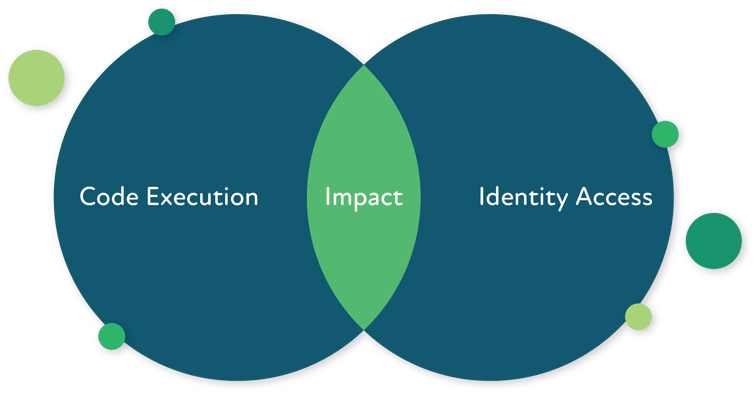
Ransomware poses a significant threat to organizations worldwide, comprised of two crucial stages. First, the adversary needs to execute code on a single system, which may have minimal impact. However, the second stage is far more damaging, as the adversary aims to access and execute code on multiple systems to cause widespread harm. It is vital to address both parts of this problem to effectively defend against ransomware attacks.
The Importance of Active Directory Security
CrowdStrike identifies that “8 out of 10 attacks leverage stolen credentials and Active Directory (AD) is one of the most common targets for these attacks.” Active Directory (AD) plays a vital role as a "source of truth" in Microsoft's database and related services, connecting network resources and access levels. It contains critical information about an organization's environment, including user data, passwords, and access levels.

CrowdStrike's ‘Global Threat Report' reveals that 80% of all breaches involve compromised identities, and identifying such breaches can take up to 250 days. Moreover, 50% of organizations have experienced Active Directory attacks in the last two years, with 40% of those attacks proving successful due to exploiting weak Active Directory (AD) hygiene. Protecting AD is of extreme importance because it controls system access. Neglecting AD security can lead to severe consequences, allowing malicious actors to steal credentials, infiltrate accounts, and move laterally within the system, potentially stealing data or causing system corruption. The urgency to address identity threats is paramount. That is where CrowdStrike’s Falcon platform comes in.
Protecting Identity: CrowdStrike’s Approach
To address identity-based threats, CrowdStrike offers a comprehensive set of solutions through its Falcon platform. CrowdStrike's Falcon platform stands as a formidable cybersecurity solution that addresses the pressing challenges posed by ransomware and identity threats. By combining endpoint protection, cloud workload security, and a data-driven approach, CrowdStrike delivers exceptional threat detection capabilities to safeguard businesses against the evolving threat landscape. Organizations can:
- Detect identity-based attacks - Falcon provides real-time visibility into identity hygiene, detecting and preventing unauthorized access attempts and suspicious behavior.
- Real-time view into identity hygiene - The platform offers unified sensor-domain controller capabilities, allowing for continuous monitoring of identities, policies, behavior, and risk.
- Prevent misuse of valid compromised credentials - CrowdStrike identifies and blocks the unauthorized use of legitimate credentials by malicious actors.
- Detect and prevent lateral movement - By monitoring identity-based lateral movement, Falcon can halt the spread of threats across the network.
- Implement identity-based segmentation - CrowdStrike helps organizations establish identity-based segmentation to enhance security and minimize the impact of potential breaches.
Enhancing Organizational Security with Redapt’s Technical Maturity Model
We have devised a solution that offers organizations an opportunity to enhance their security posture and overall operational efficiency. Redapt’s Technical Maturity model is structured across four key business dimensions encompassing over 30 domains and featuring more than 200 control questions. It is supported by a solution-based catalog, ensuring a comprehensive approach to security enhancement.
Our Technical Maturity Model offers a structured approach to enhance security and operational efficiency across various domains. CrowdStrike's Falcon platform seamlessly aligns with each step of the model, providing real-time threat detection, identity hygiene insights, and advanced security measures. By identifying business drivers, defining tailored use cases, and prioritizing security measures, organizations can leverage CrowdStrike's solutions to establish and elevate their security maturity. The platform's benchmarking, customized projects, and proactive security operations perfectly complement the model's phases.
Utilizing Redapt's Technical Maturity Model in conjunction with CrowdStrike’s Falcon platform enables organizations to not only strengthen their security posture but also achieve streamlined operations and continuous refinement of their security strategies.
Continued Progress for a Safer Tomorrow
As businesses forge ahead into the digital future, CrowdStrike emerges as an undisputed leader in endpoint protection and cloud workload security. Recognized and endorsed by Gartner and Forrester, CrowdStrike's Falcon platform equips businesses with the essential tools to combat cyber threats effectively. By pursuing a strategic roadmap to address challenges and maintaining an unwavering focus on scalability and improvement, CrowdStrike empowers organizations to navigate the intricacies of modern cybersecurity.
Categories
- Cloud Migration and Adoption
- Enterprise IT and Infrastructure
- Artificial Intelligence and Machine Learning
- Data Management and Analytics
- DevOps and Automation
- Cybersecurity and Compliance
- Application Modernization and Optimization
- Featured
- Managed Services & Cloud Cost Optimization
- News
- Workplace Modernization
- Tech We Like
- AWS
- Social Good News
- Cost Optimization
- Hybrid Cloud Strategy
- NVIDIA
- Application Development
- GPU






